Anomaly detection in O-RAN: Signaling Storm
Signaling Storm is a specific case of Denial of Service (DoS) or Distributed DoS (DDoS) attack identified by the O-RAN ALLIANCE to be addressed by xApps [1]. When firing this kind of attack, devices authorized (or not) to access the network make repeated attempts to connect to the network, „clogging up” the Random Access Channel (RACH). Secondly, the number of attackers performing signaling storms can change, impacting the attack severity. In addition, due to the multi-stage nature of the hand-shaking procedure, a whole range of redundant control information is generated in the access and core network. It is, therefore, essential to quickly locate the source of this threat and decide to reject the connection request at an early stage of registration.
In this blog, we present a signaling storm detection approach and a proposed algorithm to be implemented as an xApp for O-RAN RIC.
Note: another detection mechanism for O-RAN networks related to the jamming attack, can be found here: Anomaly detection in O-RAN: Jamming
Signaling Storm Detection Analysis and Mitigation
To detect signaling storms or DDoS attacks at the early stage of RAN (before reaching the core network), the O-RAN interfaces can be used to create so-called KPI profiles [2] that are created in Near-RT RIC and updated dynamically. Based on the monitoring of Random Access Responses, the KPI profile can capture statistics of the network access requests and Timing Advance (TA) parameters of each UE. In particular, IoT devices have this kind of profile and statistics constant. A representative example of a KPI profile is depicted in Fig 1 which comes from our work [3].

of the number of RRC Connection Requests associated with a given TA
Based on the KPI profile and the currently observed number of access requests, the so-called anomaly values (or metrics) are calculated and then input to a weighted version of the DBSCAN grouping algorithm. The algorithm decides on the presence or absence of a Signaling Storm attack. In this case, the threat analysis determines the adversary’s approximate distance from gNodeB (E2 Node). In the case of adversary UEs, an increased number of Msg2: Random Access Response messages containing the same TA parameter measured by gNodeB (E2 Node) will be observed. This way, by detecting the adversary’s activity, we can automatically identify to which group of IoT devices it belongs. (Usually, several devices located at a similar distance from the base station have the same TA.) After the detection of a signaling storm, connection requests associated with a given TA may be rejected at the stage of RAN to protect core network resources.
Signaling storm detection algorithm as xApp
The KPI profile-based signaling storm detection can be deployed as xApp [3]. The sequence UML diagram of the signaling storm/DDoS attack detection algorithm, deployed as xApp in Near-RT RIC, is shown in Fig. 2.
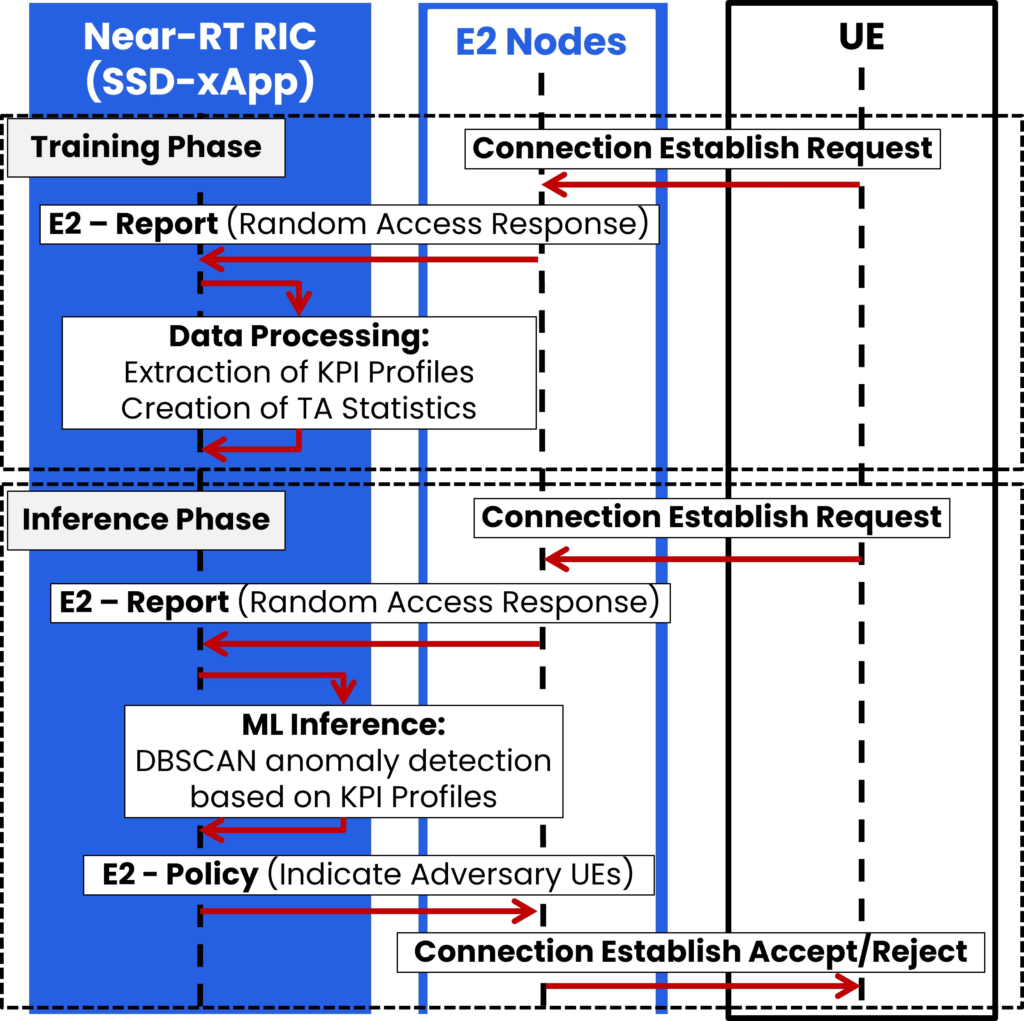
The sequence can be divided into two phases: the training phase and the inference phase. The training phase aims to build KPI profiles based on the Random Access responses forwarded to the Near-RT RIC from E2 Node (gNodeB) via the E2 interface. Within this phase, tuning the detection algorithm’s parameters is also done, e.g., adjusting the threshold for the anomaly metric above which the attack will be detected. In the inference phase, detection of the adversary’s presence takes place already at the level of the access network. It only requires the collection of Msg2 messages for a period corresponding to the KPI profile validity. If the adversary activity is detected, the xApp utilizes the E2 interface to notify the gNodeB (E2 Node) to reject connection requests from a given UE, i.e., to send an RRC Connection Reject message to stop UE authentication within the core network.
Signaling storm detection simulations
In our work [3], we tested the xApp through the computer simulations within the use case that exploits a single cell of a 2 Km radius, 100 legitimate IIoT devices, and three adversaries. Results presented in Fig. 3 show that our algorithm achieves the probability of attackers’ detection above 80% for all anomaly thresholds.
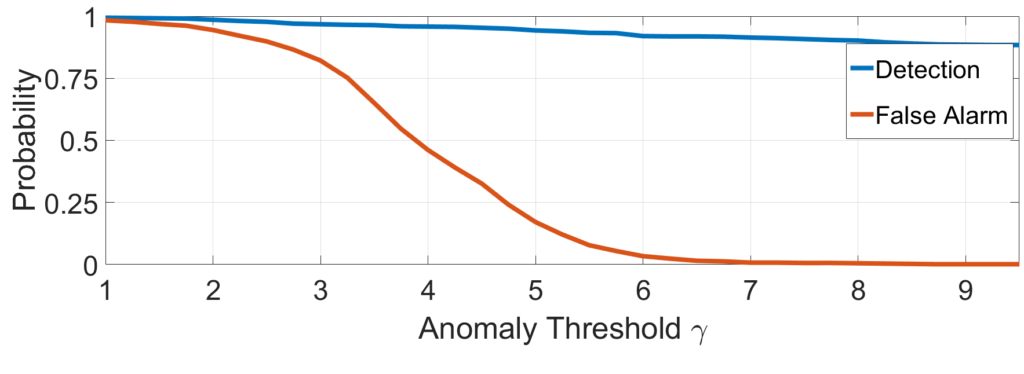
proposed xApp as a function of threshold parameter γ
However, one should notice that the probability of false alarms strongly depends on the selected threshold. From the perspective of MNO, it is often acceptable to sacrifice detection probability to avoid unnecessary alarms. Thus, the threshold of about 6.5 seems to be a reasonable choice that provides the probability of detection at the level of about 92% and a low probability of false alarm, i.e., 1.5%.
Rimedo Labs & 5G Security
Rimedo Labs participates in the 5gSTAR project on “Advanced methods and techniques for identification and counteracting cyber-attacks on 5G access network and applications”. The project is funded within the 4th CyberSecIdent program – Cybersecurity and e-Identity by the Polish National Centre for Research and Development (NCBIR) from 2021 to 2024. We believe that the openness and intelligence of RAN create opportunities for the secure operation of future networks. Stay tuned to our newly developed xApps for the secure operation of RAN, O-RAN, and future networks.
You can find more about the 5gSTAR project on this website: 5gSTAR.
You can find more details about the 5gSTAR project and our work in the 5G/6G security area in this blog post: Rimedo Labs joins 5gSTAR, a 5G cybersecurity project
References
[1] O-RAN Alliance, “O-RAN Working Group 1 Use Cases Analysis Report” v11.00, June 2023
[2] L. Bodrog, M. Kajo, S. Kocsis and B. Schultz, „A robust algorithm for anomaly detection in mobile networks,” 2016 IEEE 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications, 2016, pp. 1-6
[3] M. Hoffmann, and P. Kryszkiewicz. „Signaling Storm Detection in IIoT Network based on the Open RAN Architecture.”, IEEE International Conference on Computer Communications INFOCOM 2023, 17–20 May 2023, New York, USA 2023, arXiv e-prints: [2302.08239] Signaling Storm Detection in IIoT Network based on the Open RAN Architecture (arxiv.org)
Acknowledgments
Many thanks to the colleagues from Rimedo Labs working on the 5gStar project: Pawel Kryszkiewicz, Hanna Bogucka, and Małgorzata Wasilewska.
Other Rimedo Labs Resources on Security
- RAN openness and intelligence for 5G/6G security
- AI for O-RAN Security
- O-RAN Security and Security Offered by O-RAN
- Rimedo Labs joins 5gSTAR, a 5G cybersecurity project
- Anomaly detection in O-RAN: Jamming
Author Bio
Marcin Hoffmann is a Senior R&D engineer at Rimedo Labs working on O-RAN software development solutions and spectrum sharing-related projects. Marcin is a Graduate Student Member, at IEEE and received an M.Sc. degree (Hons.) in electronics and telecommunication from Poznań University of Technology, in 2019, where he is currently pursuing a Ph.D. degree with the Institute of Radiocommunications. He is gaining scientific experience by involvement in both, national and international research projects. His research interests include utilizing machine learning and location-dependent information for network management. In addition to that Marcin works on massive MIMO and advanced beamforming techniques. His scientific articles are published in the top journals like IEEE Journal on Selected Areas in Communications, IEEE Transactions on Intelligent Transportation Systems, or IEEE Access.

Great presentation