Anomaly detection in O-RAN: Jamming
The operating patterns of adversaries attacking the open radio interface are complicated and not obvious, e.g., an adversary carrying out a jamming attack may change the attacked band or periodically interrupt jamming. The prospective defense algorithms should be able to not only detect anomalies but also adapt to a variety of attack mechanisms. This can be done by AI/ML methods, which have been researched over the last years (e.g., see [1]-[3]).
In this post, we present an AI/ML-based jamming attack detection and analysis mechanism under development for Near-RT RIC.
Note: another detection mechanism for O-RAN networks related to the signaling storm attack, can be found here: Anomaly detection in O-RAN: Signaling Storm – RIMEDO Labs
5G vulnerability to jamming and detection algorithm requirements
The 5G system, due to broadband and adaptive transmission and advanced channel coding, is quite resistant to interference in the long run. On the other hand, the response to a disturbance may take several milliseconds. This delay may be unacceptable for Ultra-Reliable, Low Latency Communication (URLLC). As such, the detection should be carried out without additional delay, requiring Near-RT RIC to be used. In addition, this type of attack can be easy and inexpensive to carry out, thanks to the availability of Software Defined Radio (SDR) hardware, increasing its occurrence probability.
Multiple ML approaches can be used to address jamming detection. Supervised learning can be used to detect jamming as an anomaly based on signal quality parameters reported by UEs (e.g., Channel Quality Indicator – CQI and Reference Signals Received Power – RSRP). However, this requires building a database of reports with labels for both jamming and non-jamming situations. This problem does not exist if unsupervised methods are used.
A proposed approach for jamming detection
Let’s analyze the two-dimensional distribution of the UE-reported metrics to find the anomaly caused by jamming. Here, an example of CQI and RSRP values will be provided. Please note however that the type of reports can be adjusted depending on the available reports and based on the observations of their variability during jamming.
In this method, CQI and RSRP reports are collected for a given cell assuming some prespecified memory size reflecting the valid time horizon, e.g., to account for rejecting older reports that might have been collected under different propagation conditions or inter-site interference levels. If the report is not classified as collected under jamming, it is added to the current CQI-RSRP distribution estimate. A new report is compared with the current distribution, assuming its local Gaussian approximation with prespecified false alarm probability. If a given report is more distanced from the distribution than the constant false alarm threshold, it is assumed that jamming occurs.
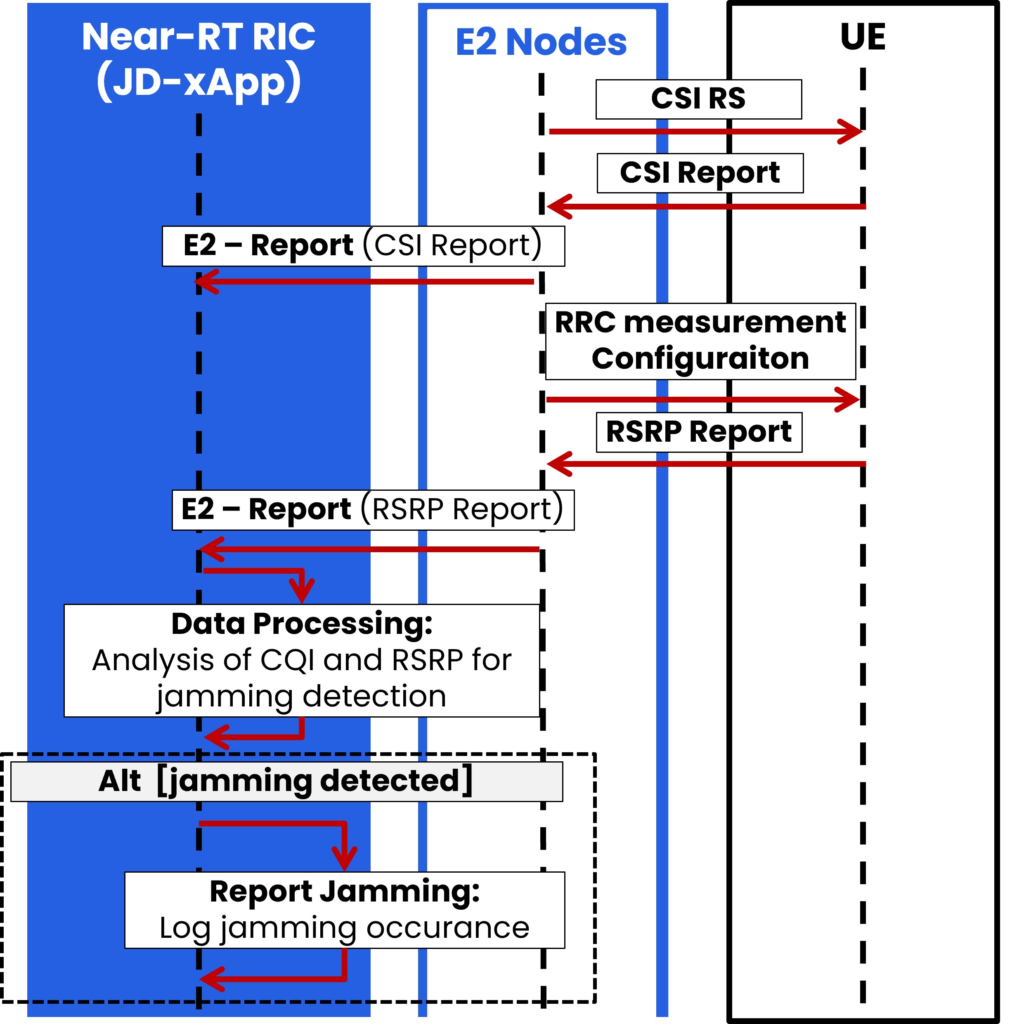
The sequence UML diagram of this method is presented in Figure 1. It shows what messages over what interfaces must be exchanged to enable jamming detection in the xApp (i.e., JD-xApp).
Jamming detection simulations
Although the probability of jamming detection of unsupervised learning may be naturally lower than the supervised learning (training-based) based method, tests show that it is highly effective in the presence of highly damaging broadband jamming.
Example results are shown in Fig. 2 (for the exact scenario definition, refer to [4]). Moreover, the probability of false jamming detection is relatively low. This requires a rather large reference measurement dataset to create a reliable RSRP-CQI distribution estimate.

The other issue is the mitigation of the detected jamming effects. Multiple solutions are possible here, from major base station reconfigurations, e.g., carrier frequency change, to Modulation and Coding Schemes (MCS) adaptations. Jammers should be automatically reported to the security monitoring entity and responsible authorities.
Rimedo Labs & 5G Security
Rimedo Labs participates in the 5gSTAR project on “Advanced methods and techniques for identification and counteracting cyber-attacks on 5G access network and applications”. The project is funded within the 4th CyberSecIdent program – Cybersecurity and e-Identity by the Polish National Centre for Research and Development (NCBIR) from 2021 to 2024. We believe that the openness and intelligence of RAN create opportunities for the secure operation of future networks. Stay tuned to our newly developed xApps for the secure operation of RAN, O-RAN, and future networks.
You can find more about the 5gSTAR project on this website: 5gSTAR.
You can find more details about the 5gSTAR project and our work in the 5G/6G security area in this blog post: Rimedo Labs joins 5gSTAR, a 5G cybersecurity project
References
[1] V. Marojevic, R. M. Rao, S. Ha, and J. H. Reed, „Performance Analysis of a Mission-Critical Portable LTE System in Targeted RF Interference,” IEEE VTC2017-Fall
[2] L. Bodrog, M. Kajo, S. Kocsis and B. Schultz, „A robust algorithm for anomaly detection in mobile networks,” 2016 IEEE 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications, 2016
[3] R. Doshi, N. Apthorpe, and N. Feamster, ‘‘Machine Learning DDoS Detection for Consumer Internet of Things Devices,’’ IEEE Secur. Privacy Workshops, May 2018
[4] P. Kryszkiewicz, M. Hoffmann, “Open RAN for detection of a jamming attack in a 5G network”, IEEE VTC2022-Spring
Acknowledgments
Many thanks to the colleagues from Rimedo Labs working on the 5gStar project: Marcin Hoffmann, Hanna Bogucka, and Małgorzata Wasilewska.
Other Rimedo Labs Resources on Security
- RAN openness and intelligence for 5G/6G security
- AI for O-RAN Security
- O-RAN Security and Security Offered by O-RAN
- Rimedo Labs joins 5gSTAR, a 5G cybersecurity project
- Anomaly detection in O-RAN: Signaling Storm
Author Bio
Paweł Kryszkiewicz received his Ph.D. (with distinction) in the field of technical sciences, the telecommunications discipline at the Poznan University of Technology in 2015. Since October 2010 he has been working at the Poznan University of Technology, currently at the Institute of Radiocommunications as an adjunct. He participated in the COST IC0902 (Cognitive Radio and Networking for Cooperative Coexistence of Heterogeneous Wireless Networks) project and projects implemented under the 7th EU Framework Program: NEWCOM # (Network of Excellence in Wireless Communications), ACROPOLIS (Advanced coexistence technologies for radio optimization and unlicensed spectrum) and COGEU (COGnitive radio systems for efficient sharing of TV white spaces in EUropean context), where it deals mainly with the problems of the physical layer of cognitive radio systems. He is also working on „Methods of receiving signals for cognitive radio systems using NC-OFDM modulation” as part of the Preludium grant from the National Science Center.
