O-RAN Security and Security Offered by O-RAN
Introduction
For Open Radio Access Networks (O-RAN) [1][2], the year 2023 began with significant events and influential publications. A very recent report on “Open RAN MoU Progress Update on Maturity, Security and Energy Efficiency” issued in February 2023 by the five signatories (Deutsche Telekom, Orange, Telecom Italia (TIM), Telefónica, and Vodafone gathered within the Telecom Infra Project (TIP)) to the Open RAN MoU (from 2021) noted the essential progress in O-RAN. This year, the most crucial topics for further development are security and energy efficiency [3]. A new Release 3 of “Open RAN Technical Priorities. Focus on Security” [4] (under mentioned MoU) focuses more on security topics and various challenges introduced by the disaggregation promoted by the O-RAN architecture. In particular, the security requirements are now contained within a dedicated section of the MoU Technical Priorities document.
In this blog post, we investigate how different players of the O-RAN ecosystem look at the security topic. Those included operators, standardization, vendors, governments, and research communities.
Note: here are the other posts on O-RAN security: RAN openness and intelligence for 5G/6G security and AI for O-RAN Security
The Voice of O-RAN ALLIANCE and Operators
Regarding security, the operators have committed (in [3]) to cooperating with national authorities, including information sharing, installation, and administration of O-RAN networks. Also, they have officially asked for O-RAN to be included in the GSMA Security Assurance Scheme (NESAS) and the European Union Agency for Cybersecurity’s 5G Certification Scheme (ENISA). The consortium has pledged to improve O-RAN networks’ security in several ways: i) to implement all mandatory measures outlined by the O-RAN ALLIANCE and 3GPP security specifications throughout their internal business processes and the supply chain; ii) to apply a zero-trust principle to each vendor in the upcoming procurement processes; iii) to include mandatory compliance with security specifications by the O-RAN suppliers (of network products and individual components); iv) to engage a wide range of vendors, including European incumbent providers and SMEs (small and medium enterprises), to ensure a multivendor strategy and v) to address any unresolved security specification gaps through the O-RAN ALLIANCE.
During the O-RAN ALLIANCE Ecosystem Briefing at the Mobile World Congress (MWC) in Barcelona on February 28, O-RAN security issues and opportunities were emphasized by Claire Chauvin, the Strategy Architecture and Standardization Director, Orange. The two basic approaches were indicated: i) security through transparency and ii) a risk-based (zero-trust) approach.
In March, the O-RAN ALLIANCE Security Work Group WG11 updated its specifications [5], which can be divided into four major sets: i) security threats models, ii) security requirements, iii) security protocol recommendations, and iv) security testing. These four pillars of the O-RAN security architecture have also been summarized earlier in 2022 in [6]. Specifically, the updates from March 2023 include the following:
- O-RAN Security Requirements Specifications 5.0
- O-RAN Security Protocols Specification 5.0
- O-RAN Security Threat Modeling and Remediation Analysis 5.0
- O-RAN Study on Security for O-Cloud 2.0
- O-RAN Study on Security for Application Lifecycle Management 1.0
- O-RAN Study on Security Log Management 1.0
- O-RAN Study on Security for Service Management and Orchestration (SMO) 1.0
- O-RAN Study on Security for Shared O-RU (SharedORU) 1.0
- O-RAN Study on Security for Near Real-Time RIC and xApps 2.0
Other specifications issued or updated in 2022 are the following:
- O-RAN Security Test Specifications 3.0 (published in October 2022)
- O-RAN Study on Security for Non-RT-RIC 1.0 (published in July 2022)
The Voice of Vendors and Manufacturers
Early this year, in January 2023, Mavenir issued a new whitepaper on “Open architecture and supply chain diversity: securing telecoms into the future” [7]. There, Mavenir’s five fundamental security principles are presented to drive the transition to open and secure systems: i) Open architecture must drive supply diversification, ii) No hardware or software should result in vendor lock-in, iii) No equipment or software should compromise entire units if it needs to be replaced or upgraded, iv) Open, interoperable systems should provide complete visibility and control of their network’s end-to-end security, and v) Open, interoperable systems should adopt a Zero Trust approach. A fascinating discussion between John Baker, the Senior Vice President of Ecosystem Business Development at Mavenir, and Hosuk Lee-Makiyama, Director of the European Centre for International Political Economy (ECIPE) on January 13th, 2023, is available in a Euractiv “The Tech Brief” podcast [8]. The debate focuses on how security needs to be built from a zero-trust basis and the role Open RAN plays in helping secure the future of telecoms in the USA and Europe.
In 2022, some other key players in the open telecommunication networks arena addressed the O-RAN security issues and opportunities. For example, in October 2022, Rakuten Symphony issued “The Definitive Guide to Open RAN Security,” which addressed the potential planes of attack and recommended strategies to mitigate risk from a total software system, configuration, and operational point of view [9]. Based on the over-decade Rakuten’s experience in building secure modern software, this handbook is supposed to guide the industry toward enduring security strategies for next-generation networks being deployed worldwide.
NEC XON informed (on September 13th, 2022) on the collaboration with Fortinet to create a demonstration and test facility of best practice Open RAN security in the NEC XON Experience Centre in South Africa [10]. The Centre includes FortiGate from Fortinet, the world’s most deployed next-generation firewall and highest performing hyper-scale firewall, which can cost-effectively secure Open RAN environment as reported by Anthony Laing, General Manager of Networking Business Unit at NEC XON – Sub-Saharan Africa.
Gavin Horn, the Senior Director of Engineering at Qualcomm Technologies, Inc., and Soo Bum Lee, Principal Engineer, at Qualcomm Technologies, Inc., in their article [11], notice that from a security standpoint, the disaggregated RAN architecture outlined in O-RAN offers numerous advantages. Disaggregation, for instance, enhances security resilience, adaptability, and agility. Moreover, O-RAN’s openness and transparency provide the path for a more secure cellular network than private implementations of a disaggregated or conventional monolithic RAN, which in part rely on „security via obscurity.”
In [12], Scott Poretsky, the Director of Security, Network Product Solutions, North America, and Joakim Jardal, the Strategic Product Manager, Security in Cloud RAN of Ericsson, consider visibility and intelligence of the service management and orchestration (SMO), such as the Ericsson Intelligent Automation Platform, play an essential role in the O-RAN security posture, providing purpose-built security functions and AI and machine learning models. A secure, standardized R1 interface between the Non-RT RIC framework and rApps enables any rApp to work with any SMO and other rApps.
The Voice of Governmental Institutions
Regarding the security of open, interoperable networks, the past year was marked by several important policies, recommendations, and statements issued at the governmental and international levels. On April 29th, 2022, UK Government published a Policy paper on “Open RAN principles,” which states, „The UK government is committed to building the security and resilience of critical network infrastructure by enhancing competition and innovation within the telecoms supply chain. Diversification of the telecoms network supply chain is essential to preserve and enhance the security, resilience, innovation, and competitiveness of telecoms networks. (…) By promoting vendor diversity, therefore, we seek to strengthen the ability of critical national networks to continue to function under threats including cyberattack and supplier exit, and for any vulnerabilities to be identified and rectified swiftly, with minimal impact.”
On September 14th, 2022, the Australian Department of Home Affairs and the U.S. Department of Commerce, as represented by the National Telecommunications and Information Administration (NTIA), issued the “Joint Statement on 5G/Open RAN Information Sharing and Telecommunications Resilience and Security Between the United States and Australia” that is the basis for strengthening collaboration between USA and Australia on technical security of Open RAN [14]. Moreover, the next day (Sept. 15th), the National Security Agency (NSA) and Cybersecurity and Infrastructure Security Agency (CISA) of the USA issued the “Open Radio Access Network Security Considerations” [15]. These considerations address the threat surface area at the interfaces between technologies and components integrated via O-RAN architecture, risks emerging from the use of open-source applications, and threats related but not unique to O-RAN.
A “Joint statement between the United States of America, Australia, Canada, and the United Kingdom on Telecommunications Supplier Diversity” was released on December 08, 2022. In that statement, the signatory countries state that they “are committed to ensuring the security and resilience of their telecommunications networks, including by fostering a diverse supply chain and influencing the development of future telecommunications technologies such as 6G. Collectively, they recognize that open and interoperable architectures are one way of creating a more open, diverse, and innovative market. (…) Today they reaffirm our commitment to these principles, outlined in the (…) 2021 Prague Proposals”. Moreover, they announced the endorsement of the abovementioned Open RAN Principles, published by the United Kingdom in April 2022 [13].
The Voice of IEEE
Ashutosh Dutta, Chair of IEEE SA Open RAN Industry Connections Activity, during the Future Network webinar on “Open RAN Challenges and Opportunities for Future Wireless Networks” [17], identified O-RAN security opportunities as i) programmability and virtualization that will adapt to dynamic nature of traffic and multi-provider access, ii) SoftRAN and cRAN in 5G networks will have embedded DDoS detection and mitigation functions, iii) Dynamic Resource Scheduling significantly reduces the risk of jamming attacks targeting mission-critical devices, iv) correlation between the control plane and the data plane traffic will enable security monitoring of traffic via correlation. He also presented several security challenges and potential mitigation techniques in place for O-RAN.
The Voice of Researchers
Last but least, a recently published survey paper [18] provides insights on i) Classification of security-related risks, ii) O-RAN possible security solutions based on blockchain, physical layer, and AI, iii) general design errors of Open RAN, their consequences, and potential mitigation are presented, and importantly, iv) a list of security benefits specific to O-RAN, and already available in V-RAN and 5G networks.
Conclusions
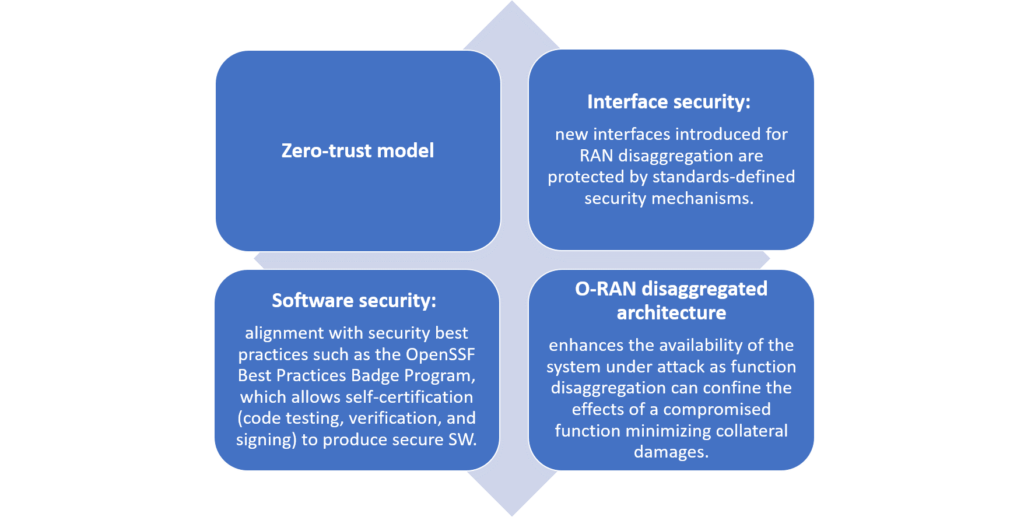
Thus, we can infer from this summary of 2022/2023 disputes, statements, and articles that the O-RAN ALLIANCE, the telecommunication business, governmental bodies, IEEE, and academic researchers speak with one voice: that the attacks surface is enlarged for O-RAN due to functional virtualization and open interfaces, but the same features can be used for the security benefits as the threats can be monitored on these interfaces and closer to the attackers (we have discussed that in our last blog on “AI for O-RAN Security” [19]). Zero-trust principle and O-RAN disaggregated architecture offer enhanced security (see Figure 1).
Indeed, it will be an exciting year for O-RAN to achieve maturity for applications in future networks. O-RAN security and security offered by O-RAN will be definitely on the agenda in the upcoming events in 2023: the O-RAN Global PlugFest Spring 2023 (at four venues Across Asia, Europe, and North America), Open RAN World collocated with 6G Summit on 26-27th of April 2023 in Berlin, FYUZ organized by Telecom Infra Project on 9th-11th of October 2023 in Madrid, TelecomTV’s fourth annual Open RAN Summit (virtual) organized on 21-22 June 2023.
Summary
The Open RAN MoU Progress Update on Maturity, Security, and Energy Efficiency issued in February 2023 noted the essential progress in O-RAN technology. This year, the most important topics for further development are security and energy efficiency. The O-RAN ALLIANCE consortium has pledged to implement all mandatory measures and apply a zero-trust principle to each vendor in the upcoming procurement processes. O-RAN security is offered through transparency and a risk-based (zero-trust) approach.
The O-RAN ALLIANCE Security Work Group WG11 updated its specifications in March 2023, while key organizations (like IEEE) and players in the telecommunication business are looking at solutions to address O-RAN security issues and exploit opportunities provided by O-RAN to increase security in future networks. These are also hot topics for academic researchers worldwide. Importantly, governments are active in issuing policies, recommendations, and joint statements regarding the security of open, interoperable telecom networks
Rimedo Labs & 5G Security
Dedicated xApps are under development in Rimedo Labs to protect the network against jamming, DoS attacks, and signaling storms, as well as against poisoning attacks on the applied FL algorithms. We are also looking at the testing methodology for our solutions with our partners.
Rimedo Labs participates in the 5GStar project on “Advanced methods and techniques for identification and counteracting cyber-attacks on 5G access network and applications”. The project is funded within the 4th CyberSecIdent program – Cybersecurity and e-Identity by the National Centre for Research and Development in 2021-2024. One of the recent results of this project is our paper published in IEEE Communications Magazine in March 2023 [20]. Stay tuned to our newly developed xApps for the secure operation of RAN, O-RAN, and future networks.
You can find more about the 5gSTAR project on this website: 5gSTAR.
You can find more details about Rimedo Labs’ work in 5G/6G security area within 5gSTAR here: Rimedo Labs joins 5gSTAR, a 5G cybersecurity project.
References
[1] M. Dryjański, Ł. Kułacz, A. Kliks, “Toward Modular and Flexible Open RAN Implementations in 6G Networks: Traffic Steering Use Case and O-RAN xApps”. Sensors. 2021; 21(24):8173. https://doi.org/10.3390/s21248173
[2] M. Dryjanski, R. Lundberg, “The O-RAN Whitepaper; Overview, Architecture and Traffic Steering Use Case”, 2021, https://www.rimedolabs.com/blog/the-o-ran-whitepaper/
[3] Open RAN MoU Signatories: “Open RAN MoU Progress Update on Maturity, Security and Energy Efficiency”, February 2023, online: https://www.orange.com/sites/orangecom/files/documents/2023-02/Joint%20MoU% 20White%20Paper%20for%20MWC%202023%20FINAL%20%5Bdigital%5D.pdf
[4] Open RAN MoU Signatories: “Open RAN Technical Priorities Focus on Security”, March 2023, online: https://telecominfraproject.com/wp-content/uploads/Open_RAN_MoU_technical_priorities_Security_Note_R3.pdf
[5] O-RAN ALLIANCE Security Work Group WG11 Specifications, online: https://orandownloadsweb.azurewebsites.net/specifications
[6] „Open RAN Security White Paper” March 2022, online: https://cdn.brandfolder.io/D8DI15S7/at/45zqtkzjp4n9ncn77mkqbx8/Open_RAN_MoU_Security_White_Paper_-_FV.pdf
[7] Mavenir whitepaper on “Open architecture and supply chain diversity: securing telecoms into the future”, January 2023, https://www.mavenir.com/resources/open-architecture-supply-chain-diversity-securing-telecoms-into-the-future/
[8] Euractive podcast, The Tech Brief, Episode 121, “Open RAN: European and American views” https://www.euractiv.com/section/digital/podcast/open-ran-european-and-american-views/
[9] Rakuten Symphony, “The Definitive Guide to Open RAN Security.” October 2022 https://assets.website-files.com/6317e170a9eabbe0fbbf4519/63582c8cec69a24b2bcde588_221025-Security-Handbook.pdf
[10] https://www.nec.xon.co.za/open-ran-best-practice-security-tests-are-now-available/
[11] G. Horn, Soo Bum Lee, “Toward enabling secure 5G networks with O-RAN”, https://www.qualcomm.com/news/onq/2022/04/toward-enabling-secure-5g-networks-o-ran
[12] S. Poretsky, J. Jardal, “Why SMO provides an ideal platform for intelligent Open RAN security”, online: https://www.ericsson.com/en/blog/2022/6/why-smo-provides-an-ideal-platform-for-intelligent-open-ran-security
[13] UK Government, Policy paper, “Open RAN principles”, 29th of April, 2022, https://www.gov.uk/government/publications/uk-open-ran-principles/open-ran-principles
[14] https://www.ntia.doc.gov/files/ntia/publications/us-australia_joint_statement_9-14-22.pdf
[15] National Security Agency and Cybersecurity and Infrastructure Security Agency (USA) “Open Radio Access Network Security Considerations”, September 15th, 2022, https://www.cisa.gov/sites/default/files/publications/open-radio-access-network-security-considerations_508.pdf
[16] Joint statement between the United States of America, Australia, Canada and the United Kingdom on Telecommunications Supplier Diversity, December 8th, 2022, https://www.ntia.gov/press-release/2022/joint-statement-between-united-states-america-australia-canada-and-united
[17] https://futurenetworks.ieee.org/images/files//pdf/Webinars/FNI-Webinar-Combined-slides-20220316_v02.pdf
[18] M. Liyanagea, A. Braekenb, S. Shahabuddinc, P. Ranaweerad, “Open RAN Security: Challenges and Opportunities”, arXiv:2212.01510v1 [cs.CR] 3 Dec 2022
[19] https://rimedolabs.com/blog/ai-for-oran-security/
[20] M. Wasilewska, H. Bogucka, H. V. Poor, “Secure Federated Learning for Cognitive Radio Sensing”, IEEE Communications Magazine, Vol. 61, no. 3, March 2023, pp. 68 – 73
Author Bio
Prof. Hanna Bogucka received her Ph.D. with honors in 1995 and Doctor Habilitus Telecommunications in 2006 from Poznan University of Technology (PUT). Currently, she is a full professor and the Director of the Institute of Radiocommunications at PUT. Moreover, prof. Bogucka is the co-founder, Board Member, and the Head of Cooperation of Rimedo Labs, a spin-off from PUT. Prof. Bogucka is involved in research in the area of wireless communications: radio resource management, cognitive radio, and green communication. She has been involved in multiple European 5th – 7th Framework Programme and Horizon 2020 projects, European COST actions, National Science Centre projects, and industry cooperation. Prof. Bogucka is the author of 200 research papers, 3 handbooks on radio communications and digital signal processing, and 3 scientific monographs on flexible and cognitive radio. Prof. Bogucka has been appointed IEEE Communications Society Director of the EAME Region and elected IEEE Radio Communications Committee Chair for the term of 2015-2016. Currently, she is the IEEE ComSoc Fog/Edge Industry Community Regional Chair in Europe, elected Member at Large of the IEEE ComSoc Board of Governors representing the EMEA region (2023-2025), and a member of the Polish Academy of Sciences.
