AI for O-RAN Security
Introduction
When talking about future Radio Access Networks (RANs) security threats one has to consider typical (or “traditional”) threats related to the radio segment of a network, as well as the expanded attack surface, due to the open architecture and interfaces in O-RAN. These considerations should be expanded by a discussion on Artificial Intelligence (AI) algorithms security issues since AI is envisioned to be embedded in multiple network tiers starting from User Equipment (UE), the gNodeB (as specialized programming modules/applications – xApps and Radio Intelligent Controllers – RICs in O-RAN), at the edge of the network in the Multi-access Edge Computing (MEC) module and in a cloud. This vision is reflected in the term Intelligent Internet of Intelligent Things (IIoIT) gaining more and more popularity.
Here below, we extend our considerations on threats and opportunities that O-RAN specifications create for network security (presented in our former blog post: RAN openness and intelligence for 5G/6G security) to deliberations on how AI at the network edge can, on one hand, be a target of attacks, and on the other, increase the network security.
Radio segment threats
The radio segment of the contemporary and future mobile communication networks is inherently exposed to attacks related to the omnipresent transmission medium. RAN and open specification of RAN (O-RAN) introduced in the 5G network [1,2] pose a challenge to their security. The typical and identified security threats for RAN are: (i) Jamming – normal, delusive (including Primary User Emulation – PUE), random, responsive, go-next, control-channel jamming, that inject unwanted signals in either the communication or control channels, (ii) Denial of Service (DoS), Distributed DoS (DDoS) exhausting network resources and making it impossible to serve users, creating traffic congestion or wasting network resources, (iii) Signaling Storm (SS) – seizing the resources for the transmission of signaling information in the control plane, (iv) Eavesdropping and traffic analysis, (v) Man in the Middle (MITM) where an adversary intercepts users’ messages, analyzes them or changes their content, e.g., by creating a fake base station, and (vi) Free-riding (spoofing) attacks to conserve local computing resources, to make up for a lack of necessary data, or to avoid violating data privacy laws. These threats are well described in the literature, and more and more efficient countermeasures are also developed (e.g., see [3]).
O-RAN-related threats
We should also note that interfaces for O-RAN, including the front-haul interface, O1, O2, A1, and E2, that are being introduced can also potentially be targets of attacks. Attackers can utilize these new open interfaces to attack the system, which could lead to a denial of service, data tampering, or data leaking, all of which have an indirect impact on the system’s security. Each O-RAN interface and function may be subject to different threats, and each threat will have a particular impact, thus, for each threat, specific security measures and solutions must be used for all aspects and assets [4].
AI/ML-related threats
AI and especially edge intelligence is envisioned to be one of the key paradigms for 5G and future 6G systems. On one hand, AI and Machine Learning (ML) algorithms can help manage the network, e.g. by improving resource allocation, improving energy efficiency, or optimizing multi-antenna transmission or beamforming. Importantly, they can also be developed to improve security, e.g. by detecting anomalies in the radio traffic. On the other hand, the use of AI/ML algorithms exposes the access network to a new type of attack – attacks on machine learning algorithms. They can be classified as (i) poisoning attacks, (ii) evasion attacks, and (iii) inference attacks [5].
The aim of poisoning attacks is to impact the learning outcomes by manipulating the data or the learning algorithm in the model training phase. The evasion attack is aimed at the inference stage (test phase) based on the previously learned model. Here, the attacker tries to bypass the model by introducing small perturbations in the input values. Inference attacks (also called reverse engineering) aim at recovering the training data and/or their labels, discovering the model architecture and its parameters (model stealing), or determining whether a sample was used to train a target ML model. This is supposed to be done by observing and using the results of the ML algorithm and model under attack.
In Figure 1, these mentioned attacks on RAN with embedded intelligence are graphically presented. As the computational capacity of centralized units (in gNodeB or MEC) is typically greater than that of the UE, all these algorithms can be designed to work together, e.g., as federated learning (FL).
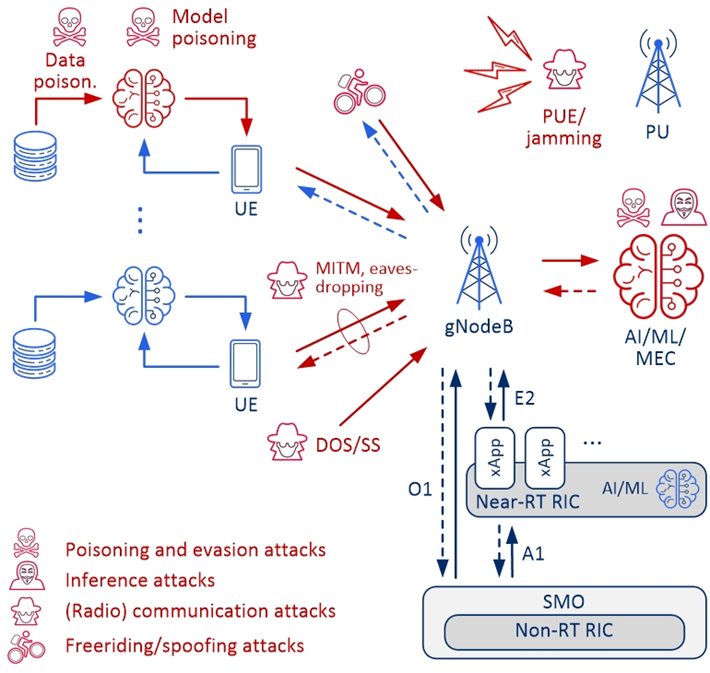
AI for O-RAN security
Let us consider how O-RAN architecture can increase security in radio access networks and connected MEC. As mentioned in our last blog post, O-RAN architecture allows for running xApps in near-real-time RAN Intelligent Controller (Near-RT RIC), which can be developed to continuously monitor and analyze security threats and protect RAN from malicious and illegal access to network segments. It makes it possible to detect threats much faster before they affect the operation of the entire network. xApps can be developed for specific types of threats in a given network that can be detected closer to the place of their occurrence. As discussed above, AI/ML algorithms, including the ones developed for O-RAN, can be the target of cyberattacks, and specific defense strategies have to be in place and onboard O-RAN platforms. Again, it is possible to develop xApps for specifying threats like this. xApps developed for RAN and O-RAN security should apply best practices for network cybersecurity, which include a zero-trust approach, continuous monitoring and security tests, data protection and privacy, and defensive mechanisms [6].
Examples of a defensive strategy against jamming or DoS attacks is to detect anomalies in the radio traffic using ML methods, such as the k-nearest neighbors (k-NN) [7], DBSCAN clustering algorithm [8], decision trees, and neural networks (NN) [9], as well as deep learning NN [10]. Convolutional Neural Networks (CNN) can be used for detecting and eliminating poisoned data and models in FL. (A specific use-case of the FL application to spectrum sensing is described in [11].) Dedicated xApps are under development in RIMEDO Labs for these kinds of security measures.
Summary
Apart from “traditional” attacks against RANs and AI/ML algorithms applied in (or close to) radio communication networks, O-RAN has even an expanded threat surface. However, O-RAN platforms can be used to increase network security with their xApps running in Near-RT RIC and developed to continuously monitor, analyze and eliminate security threats. Dedicated xApps are under development in RIMEDO Labs to protect the network against jamming, DoS attacks, and signaling storms, as well as against poisoning attacks on the applied FL algorithms.
Rimedo Labs & 5G Security
Rimedo Labs participates in the 5gSTAR project on “Advanced methods and techniques for identification and counteracting cyber-attacks on 5G access network and applications”. The project is funded within the 4th CyberSecIdent program – Cybersecurity and e-Identity by the Polish National Centre for Research and Development (NCBIR) from 2021 to 2024. We believe that the openness and intelligence of RAN create opportunities for the secure operation of future networks. Stay tuned to our newly developed xApps for the secure operation of RAN, O-RAN, and future networks.
You can find more about the 5gSTAR project on this website: 5gSTAR.
You can find more details about the 5gSTAR project and our work in the 5G/6G security area in this blog post: Rimedo Labs joins 5gSTAR, a 5G cybersecurity project
References
[1] M. Dryjański, Ł. Kułacz, A. Kliks, “Toward Modular and Flexible Open RAN Implementations in 6G Networks: Traffic Steering Use Case and O-RAN xApps”. Sensors. 2021; 21(24):8173. https://doi.org/10.3390/s21248173
[2] M. Dryjanski, R. Lundberg, “The O-RAN Whitepaper; Overview, Architecture, and Traffic Steering Use Case”, 2021, https://rimedolabs.com/blog/the-o-ran-whitepaper/
[3] J. Cao et al., „A Survey on Security Aspects for 3GPP 5G Networks,” in IEEE Communications Surveys & Tutorials, vol. 22, no. 1, pp. 170-195, Firstquarter 2020
[4] C. Benzaïd, T. Taleb, “AI for Beyond 5G Networks: A Cyber-Security Defense or Offense Enabler?.” IEEE Network, vol. 34, no. 6, Nov./Dec. 2020, pp. 140-147
[5] C.T. Shen et.al., “Security Threat Analysis and Treatment Strategy for ORAN”, International Conference on Advanced Communications Technology, ICACT2022 Feb. 13-16, 2022, pp.417-422
[6] “Open RAN Security White Paper, Under the Open RAN MoU”, by Deutsche Telekom, Orange, Telefónica, TIM and Vodafone, https://static1.squarespace.com/static/ 5ad774cce74940d7115044b0/t/623adef88d4ea05aae841f40/1648025338041/Open+RAN+MoU+Security+White+Paper+-+FV.pdf
[7] V. Marojevic, R. M. Rao, S. Ha, and J. H. Reed, „Performance Analysis of a Mission-Critical Portable LTE System in Targeted RF Interference,” 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall), 2017, pp. 1-6
[8] L. Bodrog, M. Kajo, S. Kocsis and B. Schultz, „A robust algorithm for anomaly detection in mobile networks,” 2016 IEEE 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications, 2016, pp. 1-6
[9] R. Doshi, N. Apthorpe, and N. Feamster, ‘‘Machine learning DDoS detection for consumer Internet of Things devices,’’ IEEE Secur. Privacy Workshops, May 2018, pp. 29– 35
[10] T. Erpek, Y. E. Sagduyu, and Y. Shi, “Deep learning for launching and mitigating wireless jamming attacks,” IEEE Transactions on Cognitive Communications and Networking, vol. 5, no. 1, pp. 2–14, 2018.
[11] M. Wasilewska, H. Bogucka, A. Kliks, “Federated Learning for 5G Radio Spectrum Sensing”, Sensors, 2022, 22(1), 198, pp. 1-15
Acknowledgment
Many thanks to the colleagues from Rimedo Labs working on the 5gStar project: Paweł Kryszkiewicz, Bartosz Bossy, Marcin Hoffmann, and Małgorzata Wasilewska.
Author Bio
Prof. Hanna Bogucka received her Ph.D. with honors in 1995 and Doctor Habilitus Telecommunications in 2006 from Poznan University of Technology (PUT). Currently, she is a full professor and the Director of the Institute of Radiocommunications at PUT. Moreover, prof. Bogucka is the co-founder, Board Member, and the Head of Cooperation of Rimedo Labs, a spin-off from PUT. Prof. Bogucka is involved in research in the area of wireless communications: radio resource management, cognitive radio, and green communication. She has been involved in multiple European 5th – 7th Framework Programme and Horizon 2020 projects, European COST actions, National Science Centre projects, and industry cooperation. Prof. Bogucka is the author of 200 research papers, 3 handbooks on radio communications and digital signal processing, and 3 scientific monographs on flexible and cognitive radio. Prof. Bogucka has been appointed IEEE Communications Society Director of the EAME Region and elected IEEE Radio Communications Committee Chair for the term of 2015-2016. Currently, she is the IEEE ComSoc Fog/Edge Industry Community Regional Chair in Europe, elected Member at Large of the IEEE ComSoc Board of Governors representing the EMEA region (2023-2025), and a member of the Polish Academy of Sciences.

Dear mam,
Thanking you for the nice insights.