„The O-RAN Whitepaper 2023 – Security in O-RAN”
We are pleased to introduce our second whitepaper this year: „The O-RAN Whitepaper 2023 – Security in O-RAN”. This post is dedicated to revealing some contents of the whitepaper.
Executive Summary
This whitepaper provides a technical discussion of security, one of the most important topics currently related to the Open Radio Access Network (Open RAN or O-RAN). Security has been identified as crucial for further O-RAN development. Recently, operators, international organizations, and even governments have issued several declarations and recommendations to build the security and resilience of future telecommunication network infrastructure and operation. Research and development of secure architectures and algorithms used in these networks continues. Below, we overview trends in O-RAN security R&D and present Rimedo Labs’ view on this critical topic.
First, an overview is provided of the most recent activities of the key players in O-RAN security. Key concepts for cybersecurity assurance in 5G and future 6G radio access networks are also reviewed.
Later, the whitepaper discusses two critical paradigms of 5G/6G networks, namely openness and intelligence. Their vulnerabilities and the potential to guarantee the security and privacy of communication are considered.
Next, the document focuses on Artificial Intelligence (AI) security applications in O-RAN. We elaborate on attack scenarios and security architectures using AI, assuming AI to be the subject of cyberattacks and the method for counteracting them.
Finally, we present Rimedo Labs’ selected xApps applied to detect and mitigate some example attacks on O-RAN: jamming and signaling storm. The UML sequence diagrams are provided together with simulation results exemplifying the efficiency of our algorithms.
The whitepaper ends with a summary and conclusions section along with a glossary of the used terms.
Note: The general trend of disaggregated and opening radio networks is called Open RAN. O-RAN, in turn, refers to the O-RAN ALLIANCE-specified architecture and framework.
Cite this: H. Bogucka, P. Kryszkiewicz, M. Hoffmann, M. Wasilewska, „The O-RAN Whitepaper 2023 – Security in O-RAN”, Whitepaper, Rimedo Labs, August 2023
The O-RAN Whitepaper Contents
1.0 Introduction to O-RAN Security

For Open Radio Access Networks (O-RAN) [1][2], the year 2023 began with significant events and influential publications. A very recent report on “Open RAN MoU Progress Update on Maturity, Security and Energy Efficiency” issued in February 2023 by the five signatories (Deutsche Telekom, Orange, TIM, Telefónica, and Vodafone gathered within the Telecom Infra Project (TIP)) to the Open RAN MoU (from 2021) noted the essential progress in O-RAN. This year, the most crucial topics for further development are security and energy efficiency [3].
In this chapter, we investigate how different players of the O-RAN ecosystem look at the security topic. Those included operators, standardization, vendors, governments, and research communities.
- 1.1 The Voice of O-RAN ALLIANCE and Operators
- 1.2 The Voice of Vendors and Manufacturers
- 1.3 The Voice of Governmental Institutions
- 1.4 The Voice of IEEE
- 1.5 The Voice of Researchers
- 1.6 Security in O-RAN
Chapter 2.0 Openness and Intelligence for 5G/6G Security

The architecture of the 5G network, both at the current stage (non-standalone architecture – NSA) and ultimately implemented (stand-alone architecture – SA), will be almost entirely virtualized and based on software functionalities. As a result, it is and will be vulnerable to being used, attacked, and disrupted by hackers. Regarding the security of 5G networks, most of the attention of researchers, engineers, and practitioners is focused on software cybersecurity, although attacks on the software itself are not the only problem.
This chapter discusses RAN-related aspects of 5G/6G security, including architecture-related risks, cybersecurity best practices, MEC, and O-RAN security opportunities.
- 2.1 Architecture-related Risks for 5G/6G Security
- 2.2 Best Practices
- 2.3 MEC Security Opportunities
- 2.4 O-RAN Security Opportunities
Chapter 3.0 AI for O-RAN Security
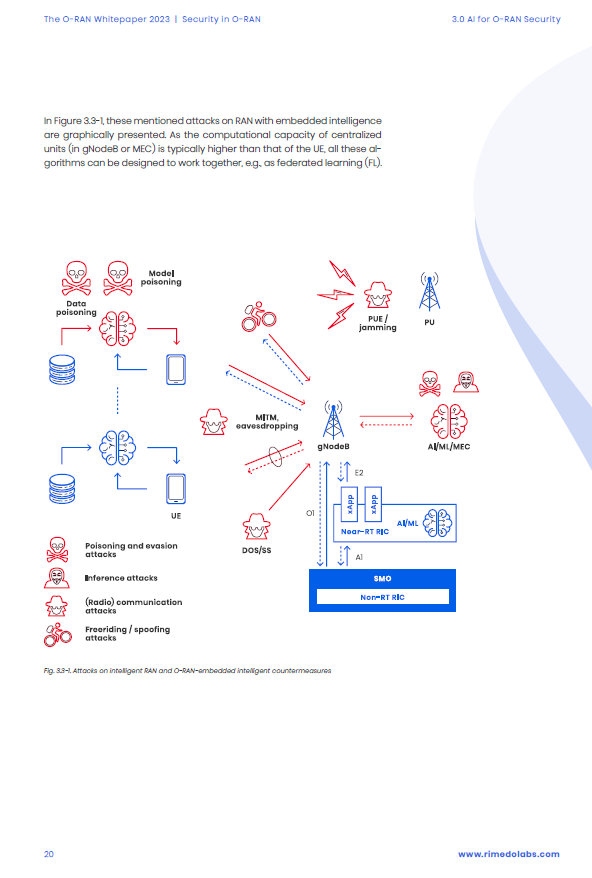
When talking about future Radio Access Networks (RANs) security threats, one has to consider typical (or “traditional”) threats related to the radio segment of a network, as well as the expanded attack surface, due to the open architecture and interfaces in O-RAN. A discussion should expand these considerations on AI algorithms security issues since AI is envisioned to be embedded in multiple network tiers starting from User Equipment (UE), the gNodeB (as specialized programming modules/applications – xApps and Radio Intelligent Controllers – RICs in O-RAN), at the edge of the network in the Multi-access Edge Computing (MEC) module and in a cloud. This vision is reflected in the term Intelligent Internet of Intelligent Things (IIoIT), which is getting increasingly popular.
In this chapter, we extend our considerations on threats and opportunities that O-RAN specifications create for network security (presented in Chapter 2.0) to deliberations on how AI at the network edge can, on the one hand, be a target of attacks and, on the other, increase the network security.
- 3.1 Radio Segment Threats
- 3.2 O-RAN-related Threats
- 3.3 AI/ML-related Threats
- 3.4 AI for O-RAN Security
Chapter 4.0 Anomaly Detection in O-RAN
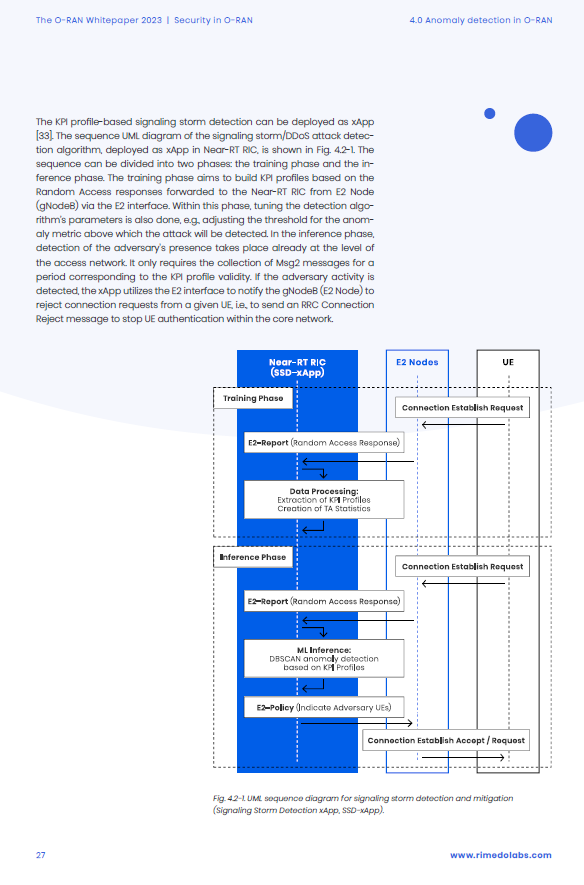
The operating patterns of adversaries attacking the open radio interface are complicated and not obvious, e.g., an adversary may change the attacked band or periodically interrupt an attack. The number of attackers can change, impacting the attack severity. The prospective defense algorithms should be able to not only detect anomalies but also adapt to a variety of attack mechanisms. This can be done, as we emphasized above, by AI/ML methods, which have been researched over the last years (e.g., see [27]-[29]).
In this chapter, we present two representative AI/ML-based attack detection and analysis mechanisms under development for Near-RT RIC.
- 4.1 Jamming Detection, Analysis, and Mitigation
- 4.2 Signalling Storm Detection, Analysis, and Mitigation
Summary and conclusions
Security is one of the key aspects within Open RAN currently in the industry’s and research activities’ agenda. The Open RAN MoU Progress Update on Maturity, Security, and Energy Efficiency issued in February 2023 indicated the importance of solving the critical issues for further O-RAN development: security and energy efficiency.
As discussed in Chapter 1.0, the O-RAN ALLIANCE WG11 is continuously updating its specifications, while key organizations (like IEEE) and players in the telecommunication business are looking at solutions to address O-RAN security issues and exploit opportunities provided by O-RAN to increase security in future networks. Governments are issuing policies, recommendations, and statements regarding the security of open, interoperable telecom networks.
The discussion in Chapter 2.0 regarding openness and intelligence as key paradigms of future 5G/6G networks presents them as the source of cybersecurity challenges and opportunities to enhance security. Open and software-based architectures expand the O-RAN attack surface while enabling increased control and monitoring of vulnerabilities. Openness increases competition in the telecommunication industry, allowing security solutions to be implemented with any vendor’s equipment. O-RAN embedded AI allows for running xApps in Near-RT RIC, enabling continuous monitoring and analysis of security threats, and detecting them faster.
Chapter 3.0 complements this topic with the application of AI in O-RAN. Apart from “traditional” radio attacks against RANs and against software or service-based architecture, cyberattacks against AI/ML algorithms (e.g., applied for 5G/6G network automation) are also envisioned. Thus, specific defense strategies must be in place and onboard O-RAN platforms and the application of AI/ML for this purpose is promising. Thus, AI appears as both the subject of and the defense against security threats.
Dedicated xApps are under development in Rimedo Labs to protect the network against jamming, DoS attacks, and signaling storms and against poisoning attacks on the applied FL algorithms. Selected xApp examples are discussed in Chapter 4.0, together with their UML sequence diagrams and selected results.
The overall conclusions from this whitepaper are as follows:
- O-RAN security and security offered by O-RAN are crucial topics for further O-RAN development. Best practices for O-RAN security are currently being formalized.
- The openness and intelligence of O-RAN create both challenges and opportunities for network cybersecurity.
- AI-exploiting xApps and rApps are promising solutions to detect and mitigate specific types of threats close to their occurrence.
Dedicated xApps are under development in Rimedo Labs. Examples are anomaly-detecting and attack-mitigating xApps for jamming, signaling storm, DDoS, and data poisoning.
References
[1] M. Dryjański, Ł. Kułacz, A. Kliks, “Toward Modular and Flexible Open RAN Implementations in 6G Networks: Traffic Steering Use Case and O-RAN xApps”. Sensors. 2021; 21(24):8173. https://doi.org/10.3390/s21248173
[2] M. Dryjanski, R. Lundberg, “The O-RAN Whitepaper; Overview, Architecture and Traffic Steering Use Case”, 2021, https://www.rimedolabs.com/blog/the-o-ran-whitepaper/
[3] “Open RAN MoU Progress Update on Maturity, Security and Energy Efficiency”, February 2023, online: https://www.orange.com/sites/orangecom/files/documents/2023-02/Joint%20MoU% 20White%20Paper%20for%20MWC%202023%20FINAL%20%5Bdigital%5D.pdf
[4] O-RAN ALLIANCE Security Work Group WG11 Specifications, online: https://orandownloadsweb.azurewebsites.net/specifications
[5] Mavenir whitepaper on “Open architecture and supply chain diversity: securing telecoms into the future”, January 2023, https://www.mavenir.com/resources/open-architecture-supply-chain-diversity-securing-telecoms-into-the-future/
[6] Euractive podcast, The Tech Brief, Episode 121, “Open RAN: European and American views” https://www.euractiv.com/section/digital/podcast/open-ran-european-and-american-views/
[7] Rakuten Symphony, “The Definitive Guide to Open RAN Security.” October 2022 https://assets.website-files.com/6317e170a9eabbe0fbbf4519/63582c8cec69a24b2bcde588_221025-Security-Handbook.pdf
[8] https://www.nec.xon.co.za/open-ran-best-practice-security-tests-are-now-available/
[9] G. Horn, Soo Bum Lee, “Toward enabling secure 5G networks with O-RAN”, https://www.qualcomm.com/news/onq/2022/04/toward-enabling-secure-5g-networks-o-ran
[10] S. Poretsky, J. Jardal, “Why SMO provides an ideal platform for intelligent Open RAN security”, online: https://www.ericsson.com/en/blog/2022/6/why-smo-provides-an-ideal-platform-for-intelligent-open-ran-security
[11] UK Government, Policy paper, “Open RAN principles”, 29th of April, 2022, https://www.gov.uk/government/publications/uk-open-ran-principles/open-ran-principles
[12] https://www.ntia.doc.gov/files/ntia/publications/us-australia_joint_statement_9-14-22.pdf
[13] National Security Agency and Cybersecurity and Infrastructure Security Agency (USA) “Open Radio Access Network Security Considerations”, September 15th, 2022, https://www.cisa.gov/sites/default/files/publications/open-radio-access-network-security-considerations_508.pdf
[14] Joint statement between the United States of America, Australia, Canada and the United Kingdom on Telecommunications Supplier Diversity, December 8th, 2022, https://www.ntia.gov/press-release/2022/joint-statement-between-united-states-america-australia-canada-and-united
[15] https://futurenetworks.ieee.org/images/files//pdf/Webinars/FNI-Webinar-Combined-slides-20220316_v02.pdf
[16] M. Liyanagea, A. Braekenb, S. Shahabuddinc, P. Ranaweerad, “Open RAN Security: Challenges and Opportunities”, arXiv:2212.01510v1 [cs.CR] 3 Dec 2022
[17] https://rimedolabs.com/blog/ai-for-oran-security/
[18] M. Wasilewska, H. Bogucka, H. V. Poor, “Secure Federated Learning for Cognitive Radio Sensing”, IEEE Communications Magazine, Vol. 61, no. 3, March 2023, pp. 68 – 73
[19] ETSI, „GS MEC 003 V2.2.1: Multi-access Edge Computing (MEC): Framework and Reference Architecture,” Group Specification, ETSI, 12.2020.
[20] J. Cao et al., „A Survey on Security Aspects for 3GPP 5G Networks,” in IEEE Communications Surveys & Tutorials, vol. 22, no. 1, pp. 170-195, Firstquarter 2020
[21] https://docs.microsoft.com/en-us/azure/security/fundamentals/network-best-practices
[22] “Open RAN Security White Paper, Under the Open RAN MoU”, by Deutsche Telekom, Orange, Telefónica, TIM, and Vodafone,
https://static1.squarespace.com/static/5ad774cce74940d7115044b0/t/623adef88d4ea05aae841f40/1648025338041/Open+RAN+MoU+Security+White+Paper+-+FV.pdf
[23] ISO 27005: https://www.iso.org/standard/75281.html
[24] Rose, S., Borchert, O., Mitchell, S., and Connelly, S., NIST SP 800-207: “Zero-Trust Architecture”, U.S. NIST, August 2020, https://csrc.nist.gov/publications/detail/sp/800-207/final
[25] C. Benzaïd, T. Taleb, “AI for Beyond 5G Networks: A Cyber-Security Defense or Offense Enabler?.” IEEE Network, vol. 34, no. 6, Nov./Dec. 2020, pp. 140-147
[26] C.T. Shen et.al., “Security Threat Analysis and Treatment Strategy for ORAN”, International Conference on Advanced Communications Technology, ICACT2022 Feb. 13-16, 2022, pp.417-422
[27] V. Marojevic, R. M. Rao, S. Ha, and J. H. Reed, „Performance Analysis of a Mission-Critical Portable LTE System in Targeted RF Interference,” 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall), 2017, pp. 1-6
[28] L. Bodrog, M. Kajo, S. Kocsis and B. Schultz, „A robust algorithm for anomaly detection in mobile networks,” 2016 IEEE 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications, 2016, pp. 1-6
[29] R. Doshi, N. Apthorpe, and N. Feamster, ‘‘Machine learning DDoS detection for consumer Internet of Things devices,’’ IEEE Secur. Privacy Workshops, May 2018, pp. 29– 35
[30] T. Erpek, Y. E. Sagduyu, and Y. Shi, “Deep learning for launching and mitigating wireless jamming attacks,” IEEE Transactions on Cognitive Communications and Networking, vol. 5, no. 1, pp. 2–14, 2018.
[31] M. Wasilewska, H. Bogucka, A. Kliks, “Federated Learning for 5G Radio Spectrum Sensing”, Sensors, 2022, 22(1), 198, pp. 1-15
[32] P. Kryszkiewicz, M. Hoffmann, “Open RAN for detection of a jamming attack in a 5G network”, IEEE 97th Vehicular Technology Conference (VTC2022-Spring).
[33] M. Hoffmann, and P. Kryszkiewicz. „Signaling Storm Detection in IIoT Network based on the Open RAN Architecture.”, IEEE International Conference on Computer Communications INFOCOM 2023, 17–20 May 2023, New York, USA 2023, arXiv e-prints: arXiv-2302
To download the Whitepaper, go to this link.
Other Resources from Rimedo Labs
- The previous whitepapers: The O-RAN Whitepaper 2023: Energy Efficiency, The O-RAN Whitepaper 2022 (RAN Intelligent Controller), The O-RAN Whitepaper 2021,
- To check our blog posts on #AllThingsWireless, visit: Blog – RIMEDO Labs
- Webinar: A video recording from an O-RAN Webinar: O-RAN Architecture and Use Cases – YouTube
- To download the slides from the O-RAN Webinar, visit: slides on O-RAN Architecture and Use Cases
- Training: Sign up for our O-RAN System Overview Course.
- Poster (High quality, printer-friendly, A3): Subscribe to get your O-RAN Poster copy.
Author Bio
Marcin Dryjanski received his Ph.D. (with distinction) from the Poznan University of Technology in September 2019. Over the past 12 years, Marcin served as an R&D engineer and consultant, technical trainer, technical leader, advisor, and board member. Marcin has been involved in 5G design since 2012 when he was a work-package leader in the FP7 5GNOW project. Since 2018, he is a Senior IEEE Member. He is a co-author of many articles on 5G and LTE-Advanced Pro and a co-author of the book „From LTE to LTE-Advanced Pro and 5G” (M. Rahnema, M. Dryjanski, Artech House 2017). From October 2014 to October 2017, he was an external advisor at Huawei Technologies Sweden AB, working on algorithms and architecture of the RAN network for LTE-Advanced Pro and 5G systems. Marcin is a co-founder of Grandmetric, where he served as a board member and wireless architect between 2015 and 2020. Currently, he serves as CEO and principal consultant at Rimedo Labs.
